5 Effective Ways to Clone A Phone

The advancements that we are bestowed within this era speak of something so surreal clone a phone that expands beyond the boundaries of human comprehension. Science and technology have made us comfortable and eased in our lives and we cannot help but thank the majestic innovations for the benefits they bestow on society.
Thank you for reading this post, don't forget to subscribe!However, everything comes along with a negative connotation. Many innovations are considered detrimental and are reviewed deregulatory for their expected perils and complications. Mobile phones are the foremost equipment of science that are considered dangerous for humans, teenagers in particular. Phones, apart from their impressive and massive uses, are highly menacing if their usage is left unchecked.
If you are worried about your spouse or teenage child and you want to explore the secrets that dwell within their mobile phones, a tool is required. There are many tools in the market that would help produce an exact copy of the target mobile and aid you to access it remotely. If you want to check those applications, scroll downwards!
- Cocospy- An Effective Cloner!
Cocospy is an effective strategy that can be employed if you want an exact copy of the target mobile. Cocospy is a huge and appreciated brand that has been acknowledged by millions of persons from all across the globe. This brilliant application would help you secure the target mobile details anonymously.
Many people who lack the knowledge and proper guidance about phone hacking may ask frivolously “how to clone a phone?” This question is brilliantly answered by Cocospy as it aids you effectively in gaining direct entry to the target smartphone. Cocospy runs without rooting or any other concealed need.

The text provided below is fully equipped with the challenges of the questions you are building up in your mind and would try to provide a detailed explanation. However, if you are still concerned about our authenticity and need a helping hand, visit this page to get all of your queries dealt and answered!
Why Cocospy?
Cocospy and its expertise are clearly announced by advanced technological marketplaces like Android Authority, CNET, PCMag, TechRadar and many others. This clarifies the notion of Cocospy being the best and the most used application for spying and phone hacking.
Cocospy is an oriented and equipped firm that helps you to gain a viable entry to the phone of your interest. Cocospy is full laced with features that are normally difficult to be found in certain spying applications.
Cocospy is known and recognized by millions of people across the world. With the fan following expanding across the globe and an unprecedented increment in the popularity, Cocospy secures a reputed place in the nexus of all the spying facilities.
Cocospy can be operated from all kinds of operating systems and can be used for remote task procedure and performance options. Cocospy runs without any need for physical access and therefore can be used from a distance while the target is completely unaware of it.
Cocospy possesses 35+ valiant and extensive features and options that it can secure all of the information within the target phone through remote acquisition.
If any problem is faced and you want an immediate retreat, you can Un-install Cocospy from the control panel.
How Is All Of This Done?
Part 1: Setting Up:
The setup of an application is the first thing to perform as there is going to be a lot of other applications in the market as well. Choosing Cocospy as your first mode of escape from the harsh reality is the best choice. Cocospy works without any assistance from the external links and can be easily installed.
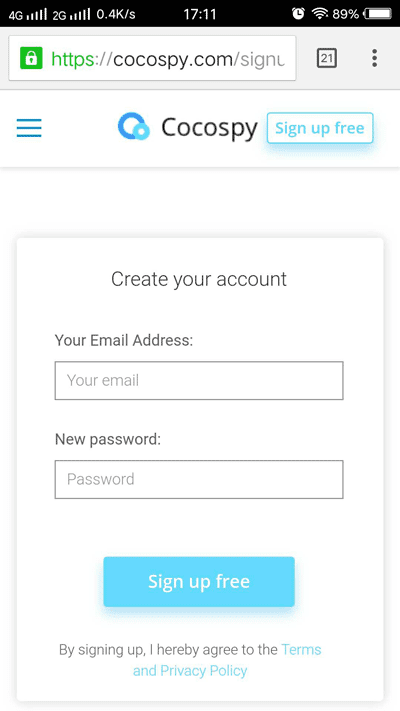
Cocospy, due to its easy and web-based accessibility, provides all kinds of assistance without any direct access to the target phone. This means that you can easily hack the target phone anonymously. Cocospy is used and adorned for its features. Installing Cocospy is the easiest task in the setup.
Part 2: Credentials And Detailing:
The most crucial and detailed step of any setup is the part in which you forego your privacy to divulge the details. However, Cocospy confirms that no privacy breach is observed and the data is kept secure from any external attack. The detail window opens as soon as you install the application for the detail providence.
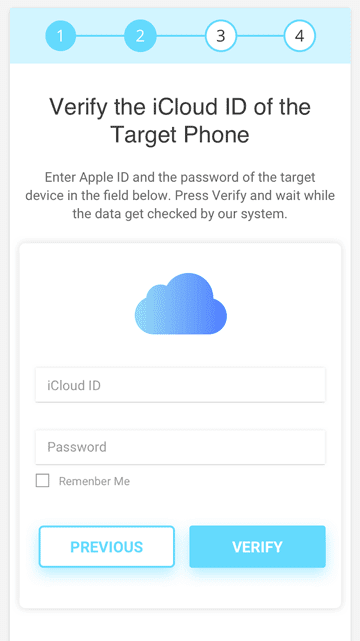
Cocospy requires G-mail details and credentials from the persons who use the Android operating system. Subsequently, iCloud credentials can be provided if you are an iPhone user.
Cocospy assures that no compromise is faced on the protection of credentials.
Part 3: Completion:
Completion of the process occurs when you provide and secure all of the details from the account to confirm your unique identity. Cocospy makes sure that all of your problems are dealt with a superior solution and cutting-edge technology that can be employed all around.
Completing immediately makes the things get done in minutes!
Part 4: The Dashboard Facility:
Cocospy possesses a superlative facility for its users that it can be accessed from almost anywhere and can be used to procure intimate details. Cocospy provides a dashboard so that all of the activities can be monitored from the phone and you can easily watch all of the arsenals being used form all around.
A complete surveillance detail is shown on your phone screen while your target remains unaware of the fact that he or she is under 24/7 surveillance.
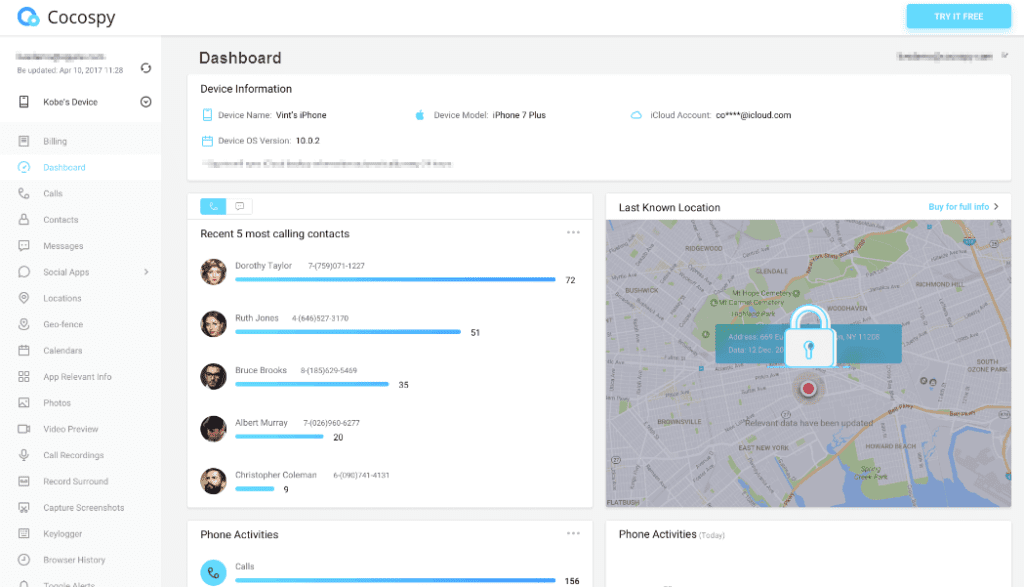
Use this dashboard for all kinds of spying.
- Spyier:
Spyier is another branded technology that helps you to hack into the Facebook messenger of the persons whom you consider suspicious. This application is full of new benefits and advantages that are uncommon in other competitors.
Spyier brand is a well-recognized brand, gaining the same amount of followers from around the planet like Spyic and aiding in an easy hack.

Spyier has gained an impressive amount of fan following and therefore can be trusted for all of your hacking needs and procedures.
- Minspy:
Minspy is known and reputed by many persons from all parts of the globe. As its name defines, it is a minute and comprehensive application that can be employed into the target phone for hacking and divulgence of the target ID.
You can always use Minspy for your hacking procedures if you want a diligent and easy mode of divulging the password for personal reasons. Minspy is a known and recognized firm that is on its way to further progress.

Employ Minspy in your hacking procedures if you need something compact yet impulsive!
.4. Spyine:
Spyine is a good new facility that is known for making its customers come back again as it poses a grave comfort to the persons in need. Spyine is a revolutionary application with new improvisations and techniques that make it the most satisfactory application.

Spyine can help you to easily hack the target ID of the target persons from where you can easily access their stories and media files that are shared across. Spyine is all that you require for a cosy and yet impressive feat of spying and cloning a target phone.
You can always trust and employ this unique technology in your daily tasks for ease and superiority in phone cloning.
- Spyic:
Spyic is known and recognized by a variety of technology firms that are Android Authority, CNET, PCMag, TechRadar and more. This speaks of a highly responsible and trusted application that would help you to gain easy access to the target mobile. You can secure all of the details from the target phone if you employ Spyic in your daily spying routine.
Spyic is an all-time favourite and reputable facility that has gained an impressive amount of followers from all across the world. Spyic is an old utility that has gained heaps of experience in the field for its massive strategic formulae and entitlements.

Nothing can beat Spyic in superiority and competence.
Conclusion:
These five applications are all set for easing the problems that you face during any hacking procedure. All of these applications are handpicked by technological experts and marketing professionals to make sure that your demands are met with superior and high-end satisfaction.
Make sure that you are reinforced by the ecstatic privileges these applications bestow upon you and Make sure to make good use of this virtuoso and keep a check on your target under secrecy!
